This is a happy path demo of setting up Okta as the Idp for AWS Control Tower (via AWS SSO).
Goal: To utilize users and groups in Okta to manage AWS control tower.
1. Create a brand new Control Tower instance
In this demo, we create the AWS Control Tower instance in a brand new AWS account. During this process, control tower creates several services/components, such as AWS Organizations, AWS SSO, default organizations unit (OU) “Security” and 2 AWS accounts “Log Archive” and “Audit”.
In the AWS SSO, some default SSO user groups are created for managing Control Tower:
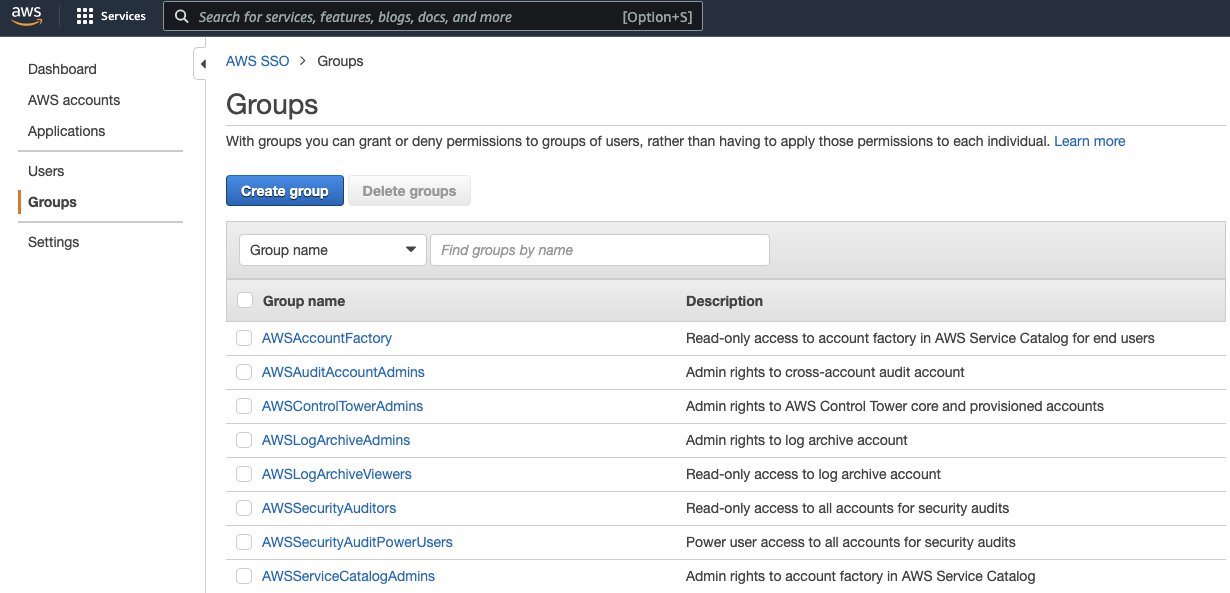
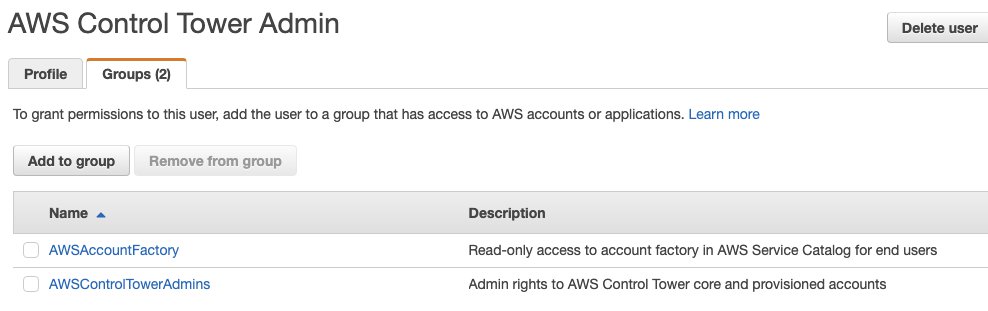
The default admin user for organization management account is “AWS Control Tower Admin”.
Detailed user info
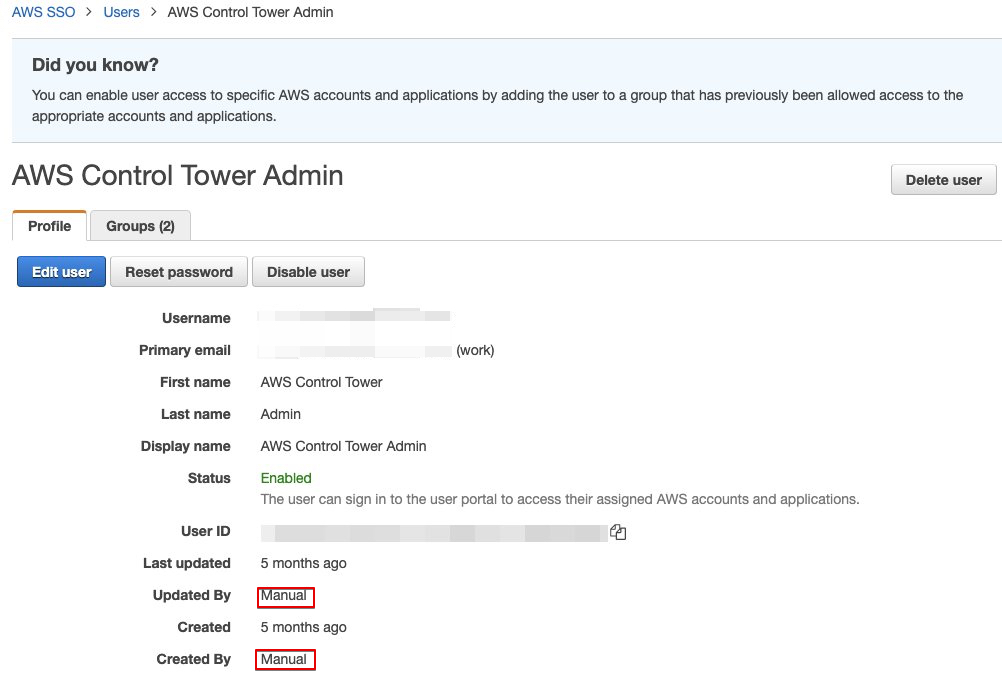
And it belongs to 2 groups: AWSAccountFactory and AWSControlTowerAdmins
2. Setup Okta and use it as the idp of AWS SSO
2.1 Create an environment of Okta]
For this demo, we are using a free developer plan of Okta.
2.2 Setup Okta as the idp of AWS SSO
Follow the steps in the following document, to use Okta as the idp of AWS SSO.
Note that you need to check steps from both documentation to make sure the integration and user provisioning works.
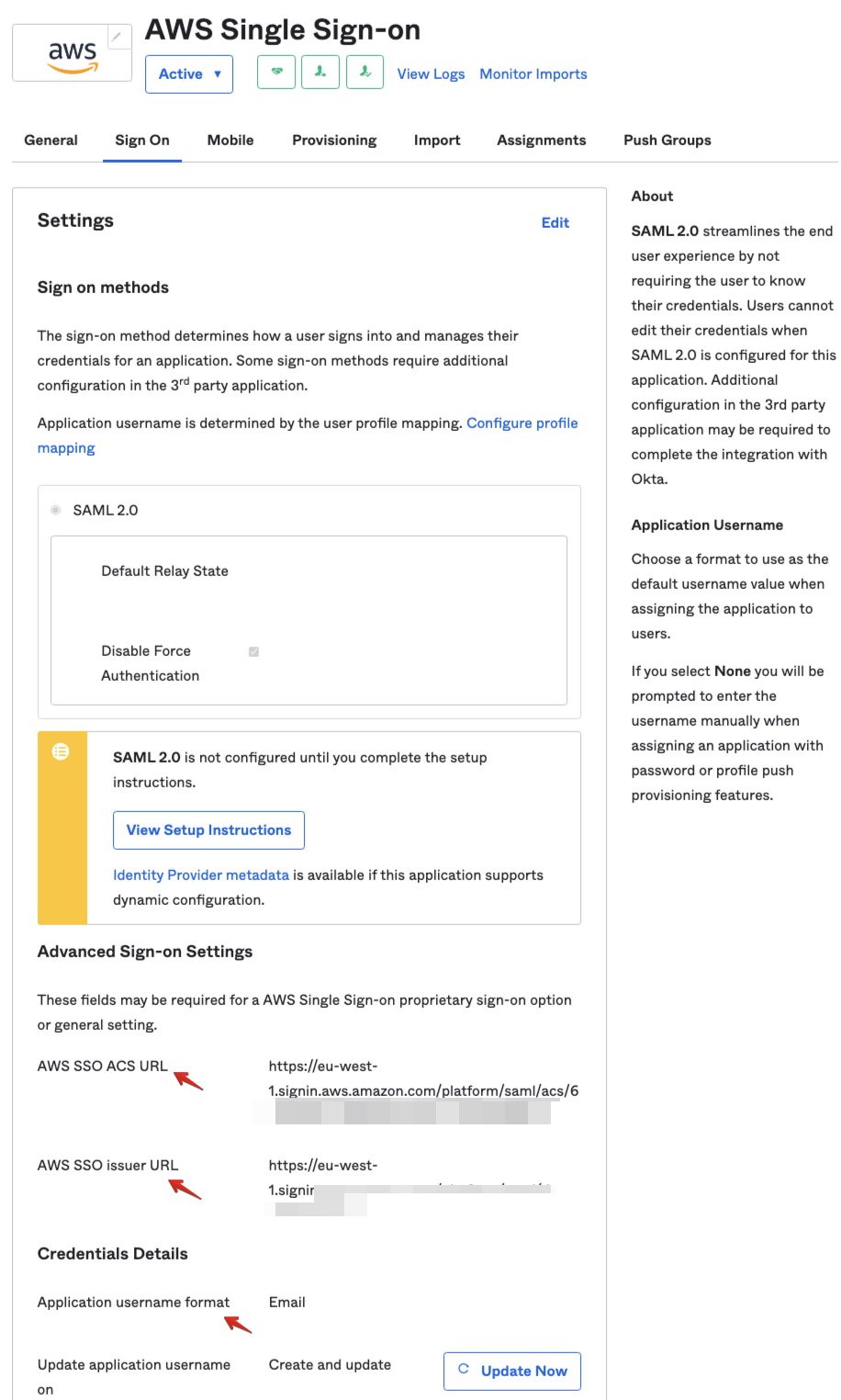
2.2.1 Basic hand-shake, import metadata file from Okta to AWS SSO
Steps: How to Configure SAML 2.0 for AWS Single Sign-on
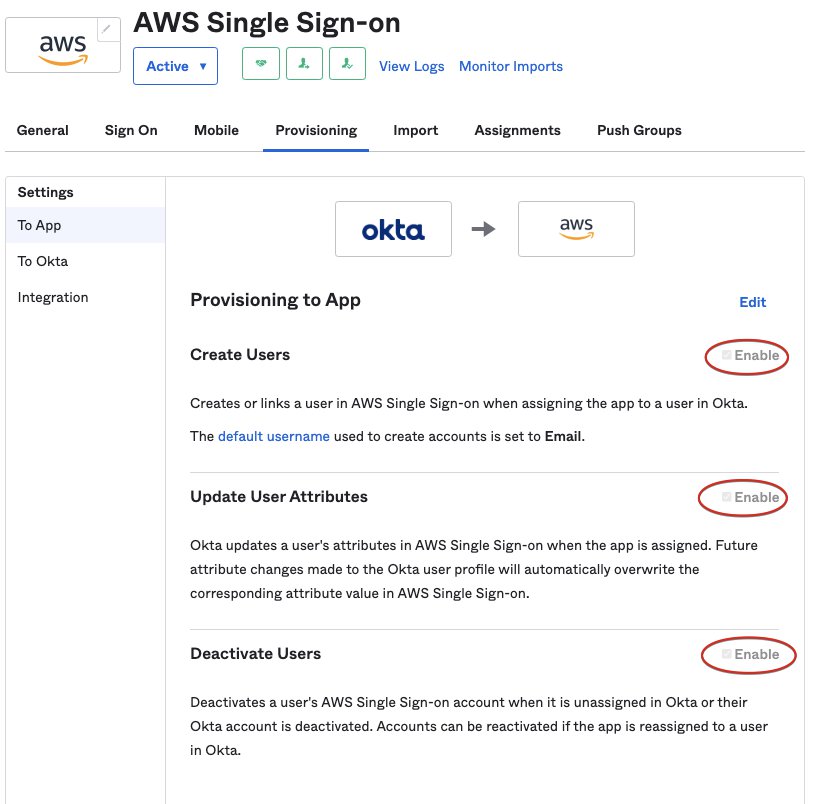
2.2.2 Config provisioning and other settings in AWS SSO
Steps: Configure provisioning for Okta in AWS SSO
2.3 The basic setup is ready, but not for users and groups yet
After the basic hand-shake between AWS SSO and Okta, the AWS SSO is now using Okta.
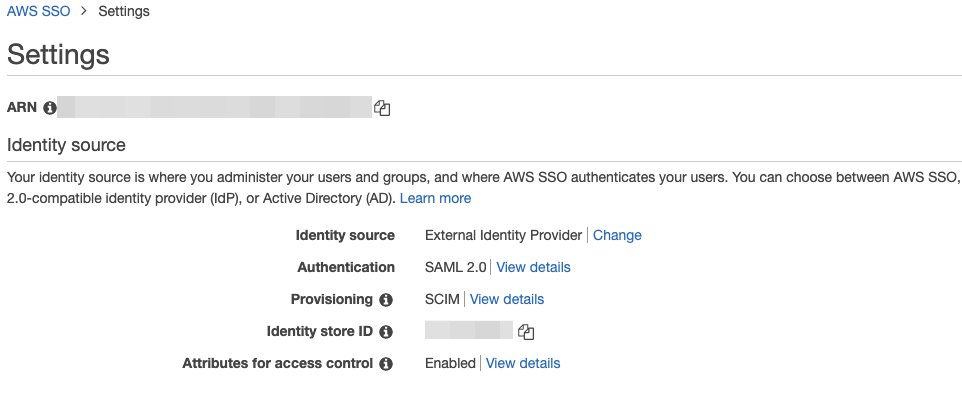
In Okta groups UI, you can see identical groups as in AWS SSO are created in Okta. The Everyone is a default Okta user group.
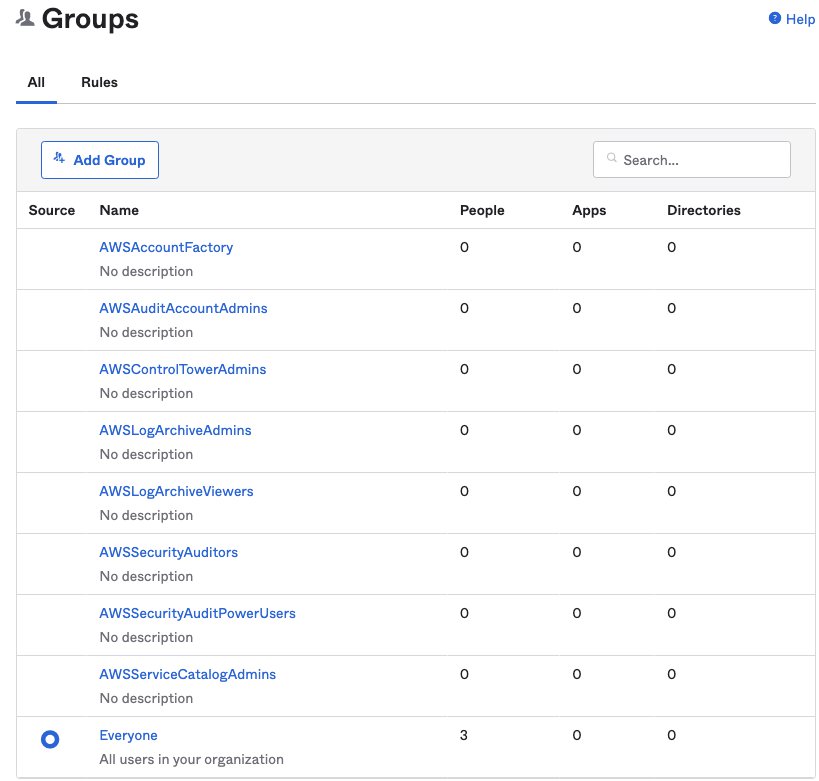
Note: you cannot add/remove users to it, as it says “This group is managed automatically by Okta, so you cannot edit it or modify its membership.”
3. Setup Okta users and groups, push them to AWS SSO
3.1 Create user and groups in Okta
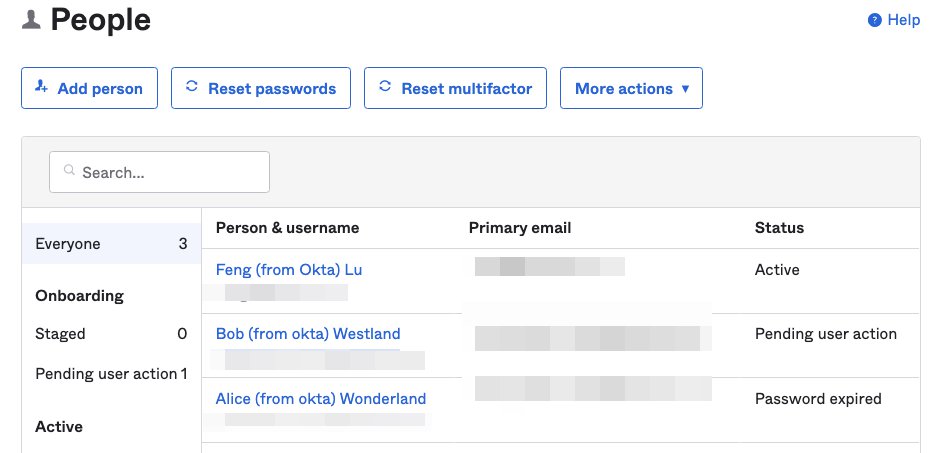
Lets create some test users:
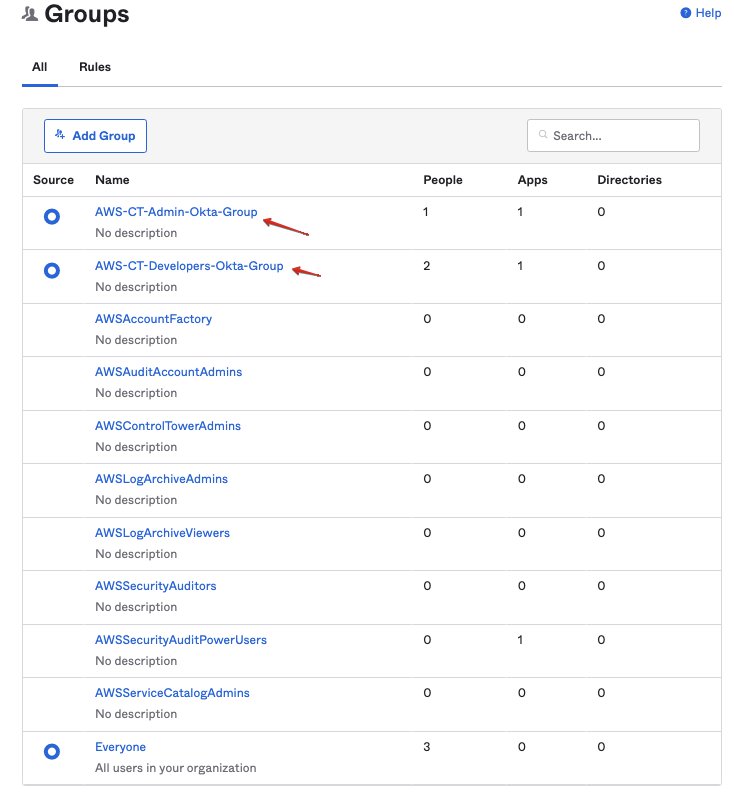
We also create user groups in Okta
- AWS-CT-Admin-Okta-Group, has 1 user: Feng
- AWS-CT-Developers-Okta-Group has 2 users: Alice and Bob
However, they are not appearing in AWS SSO user list. There is still no Okta user nor Okta group.
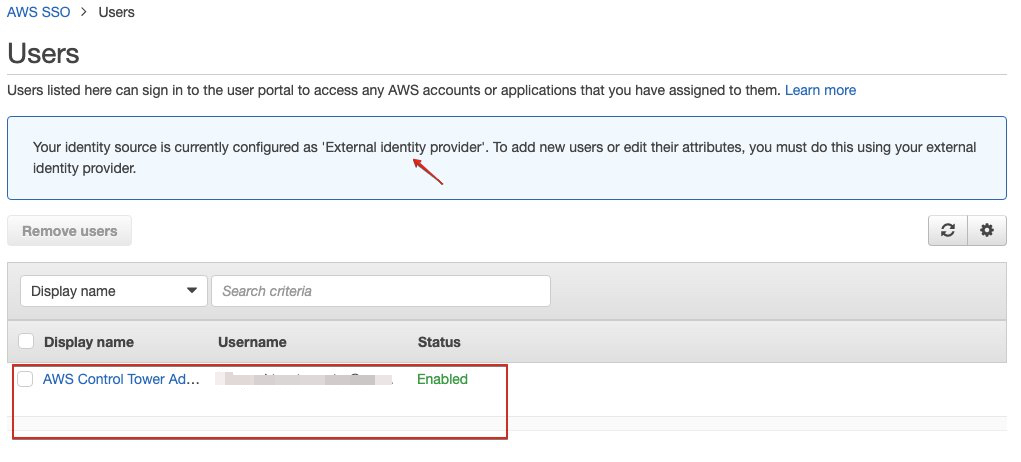
In order to user the users from Okta, these users need to be assigned to AWS SSO Application in Okta.
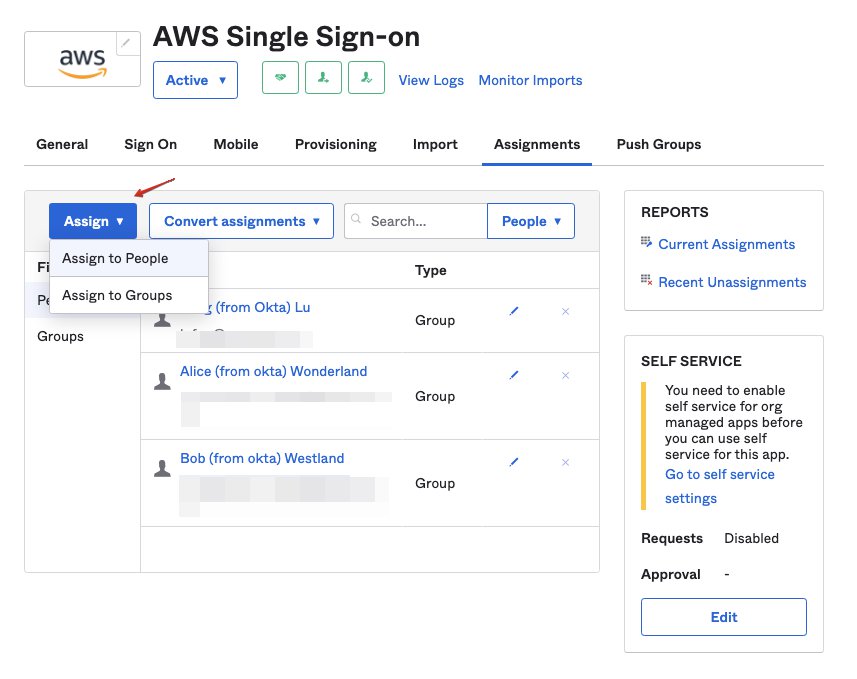
3.2 Assign users and/or groups in Okta
Go to Okta -> Application -> AWS SSO, in Assignments tab, you can either assign individual users or user groups. In this screenshot, all users are assigned to AWS SSO via Group (see the Type column).
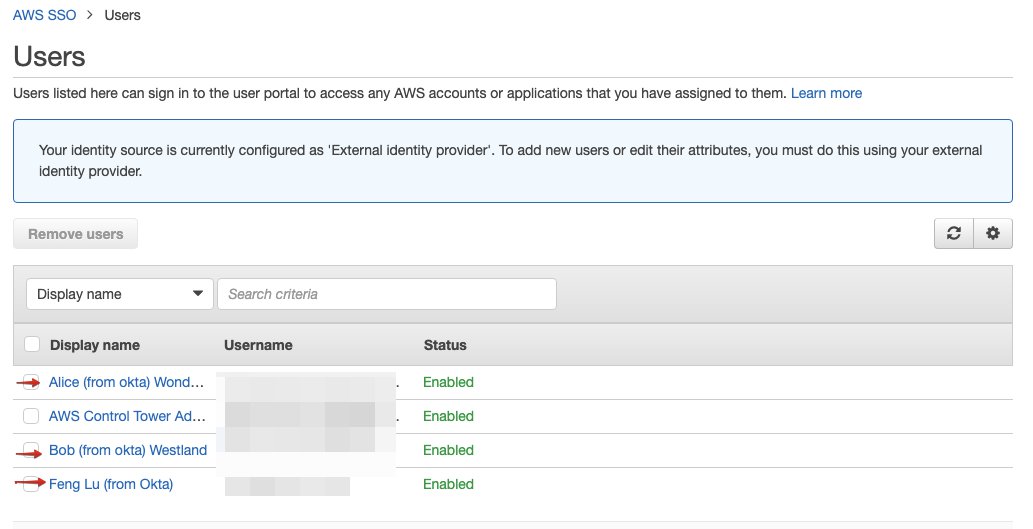
Soon, you can see these 3 users appear in AWS SSO interface.
The detailed info. Note that it was created and updated by SCIM.
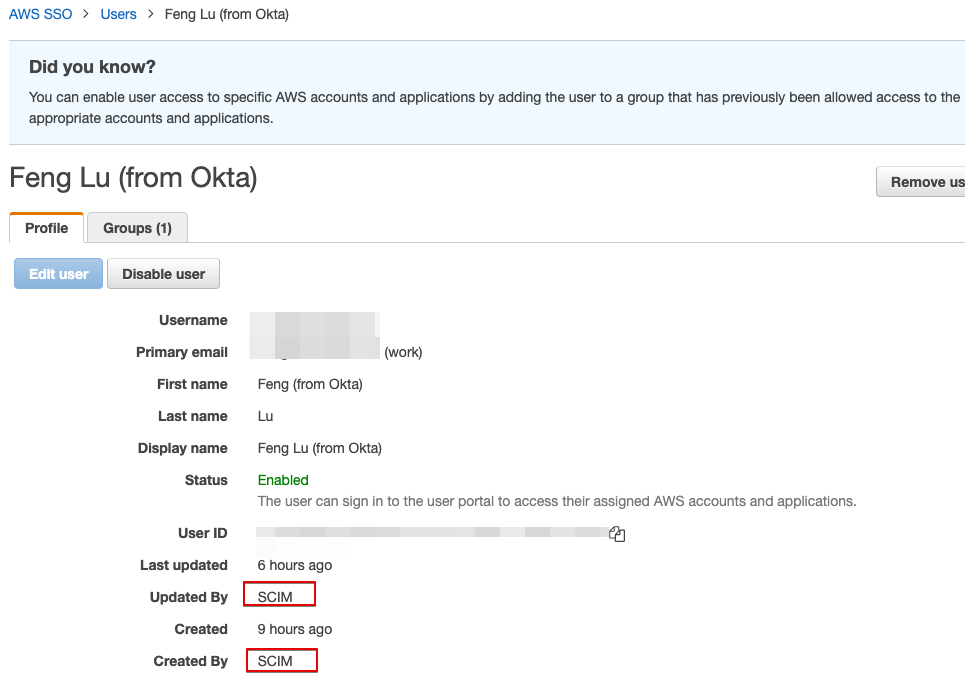
Now you can assign them into AWS account, so the user can login to AWS console via login to Okta.
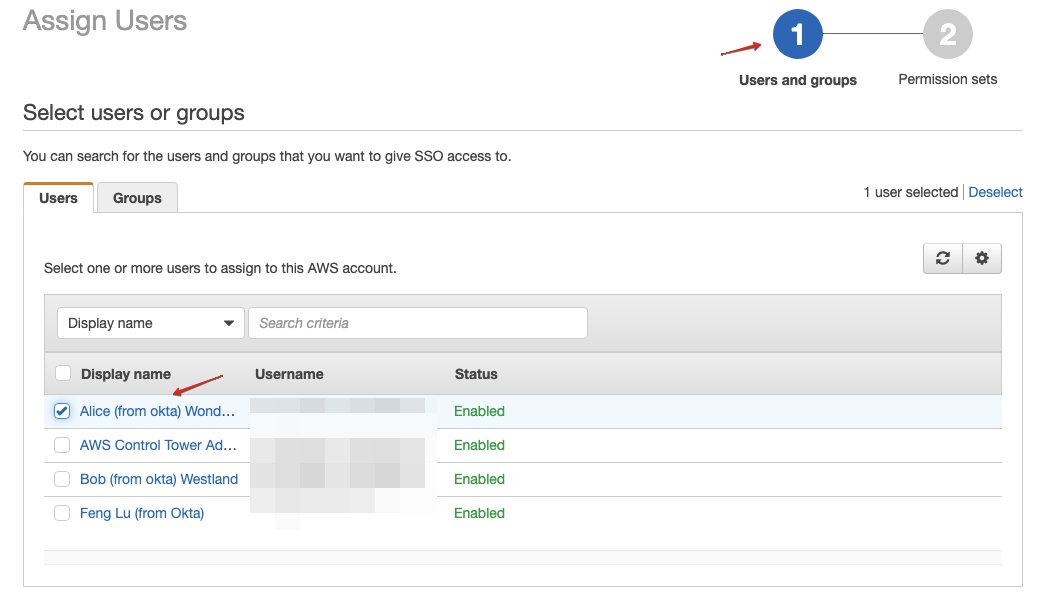
3.3 Push groups from Okta to AWS SSO
Now we can grant permission for individual Okta users. But how about Okta group? These new okta groups are not available in AWS SSO yet. And the groups with identical names from AWS SSO is not helping, as we cannot add users into it.
To solve this, we need to push the Okta groups to AWS SSO by setting up the “Push Groups”.
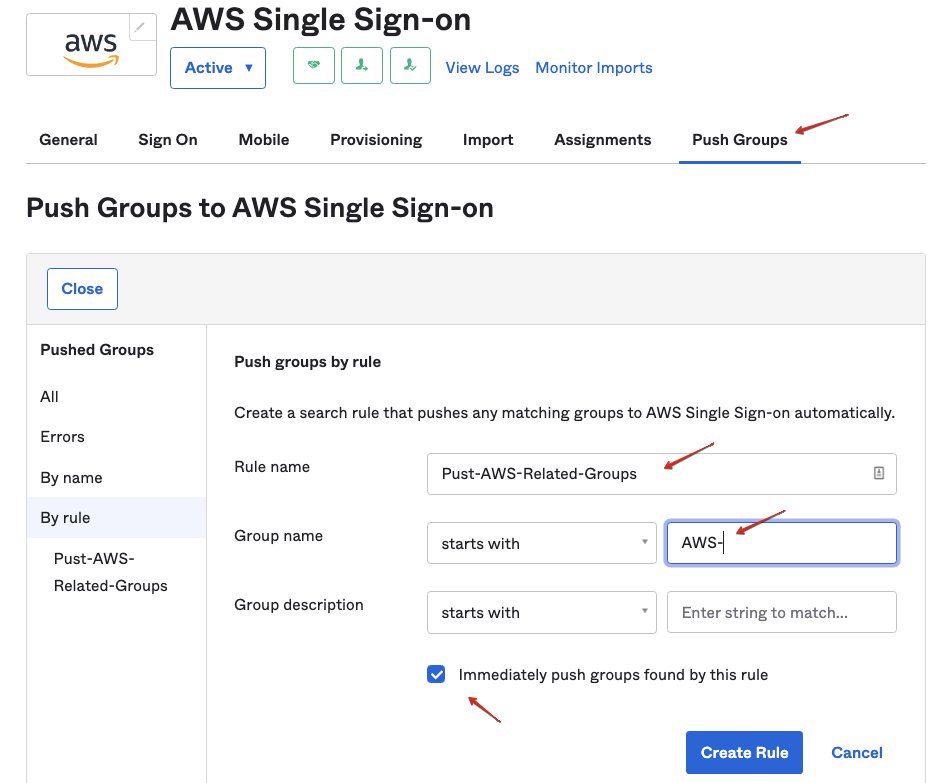
Go Okta > Application > AWS SSO, in tab “Push Groups”, here you can push group by name, or setup roles for batch pushing.
In this demo, we setup a rule named “Pust-AWS-Related-Groups” for pushing any group that starts with “AWS-”
Soon, these groups were pushed to AWS SSO:
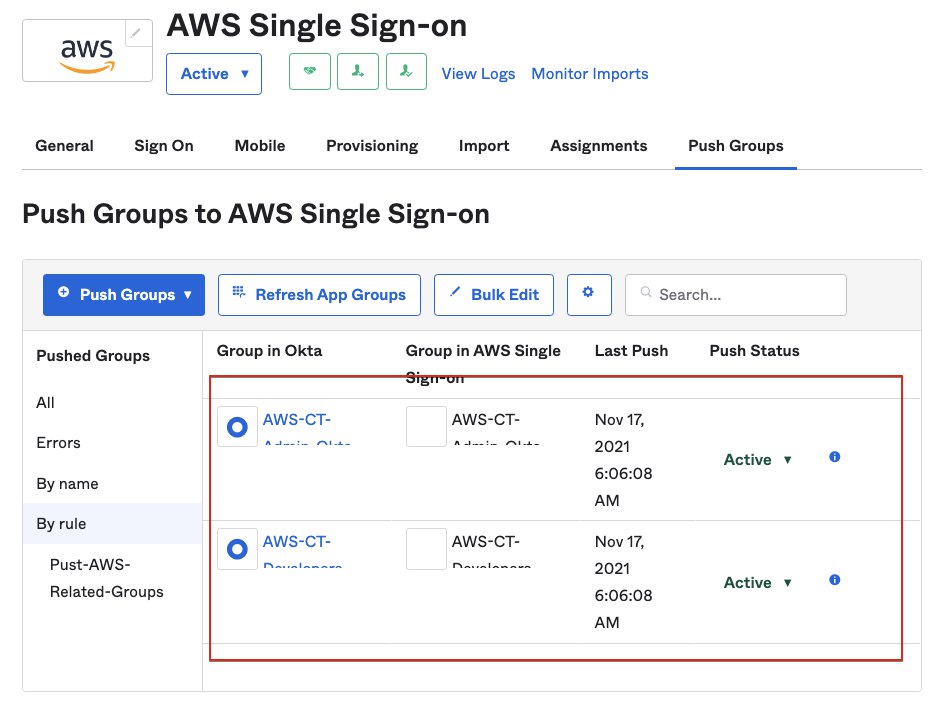
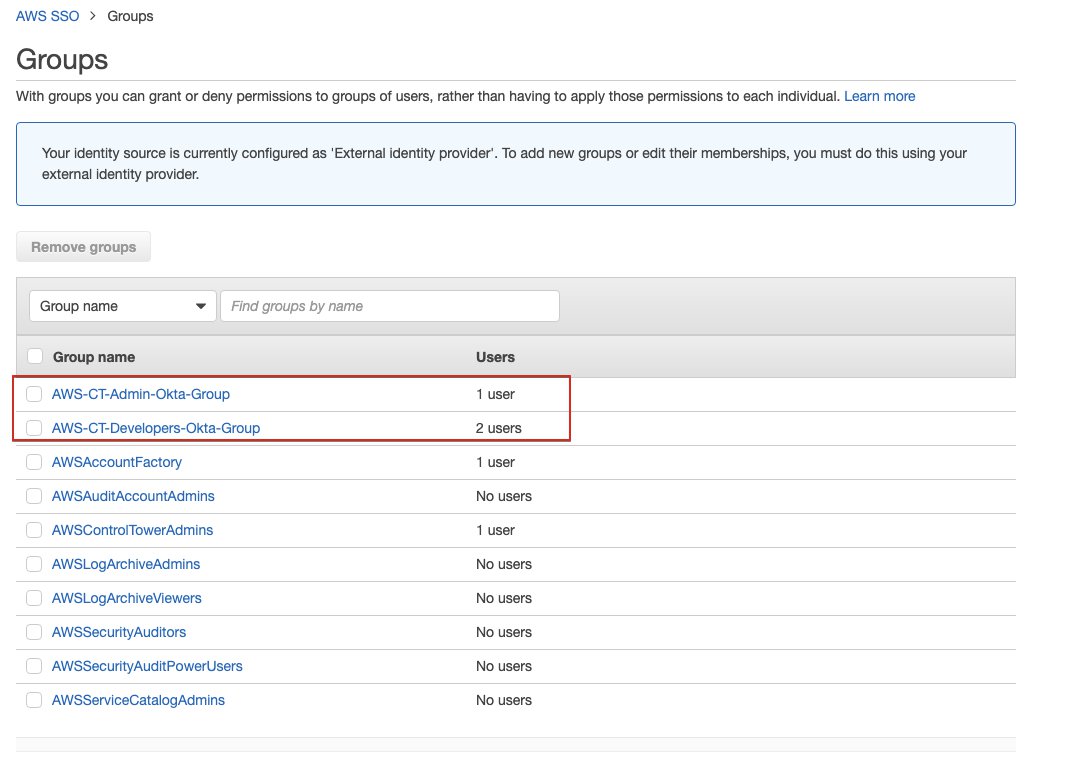
Now you can also grant permission to groups, such as every Okta user in AWS-CT-Admin-Okta-Group now have permission as AWS control tower admin.
EoF.