In Application Insights, you can create an availability web testing to monitor the availability of a web application. It supports 2 type of testing:
- URL ping test: a simple test that you can create in the Azure portal.
- Multi-step web test: which you create in Visual Studio Ultimate or Visual Studio Enterprise and upload to the portal.
Normally it is easy to setup ping test and multiple step testing against a public site.
However, in order to have a multiple step testing against an ADFS federated application, you will have to do some extra in order to take care of the authentication part.
The problem
By default, the test scripts that you recorded via Visual studio cannot handle the ADFS authentication. Depends on the version of your Visual Studio, the generated script either has no token, or has a token with a timestamp.
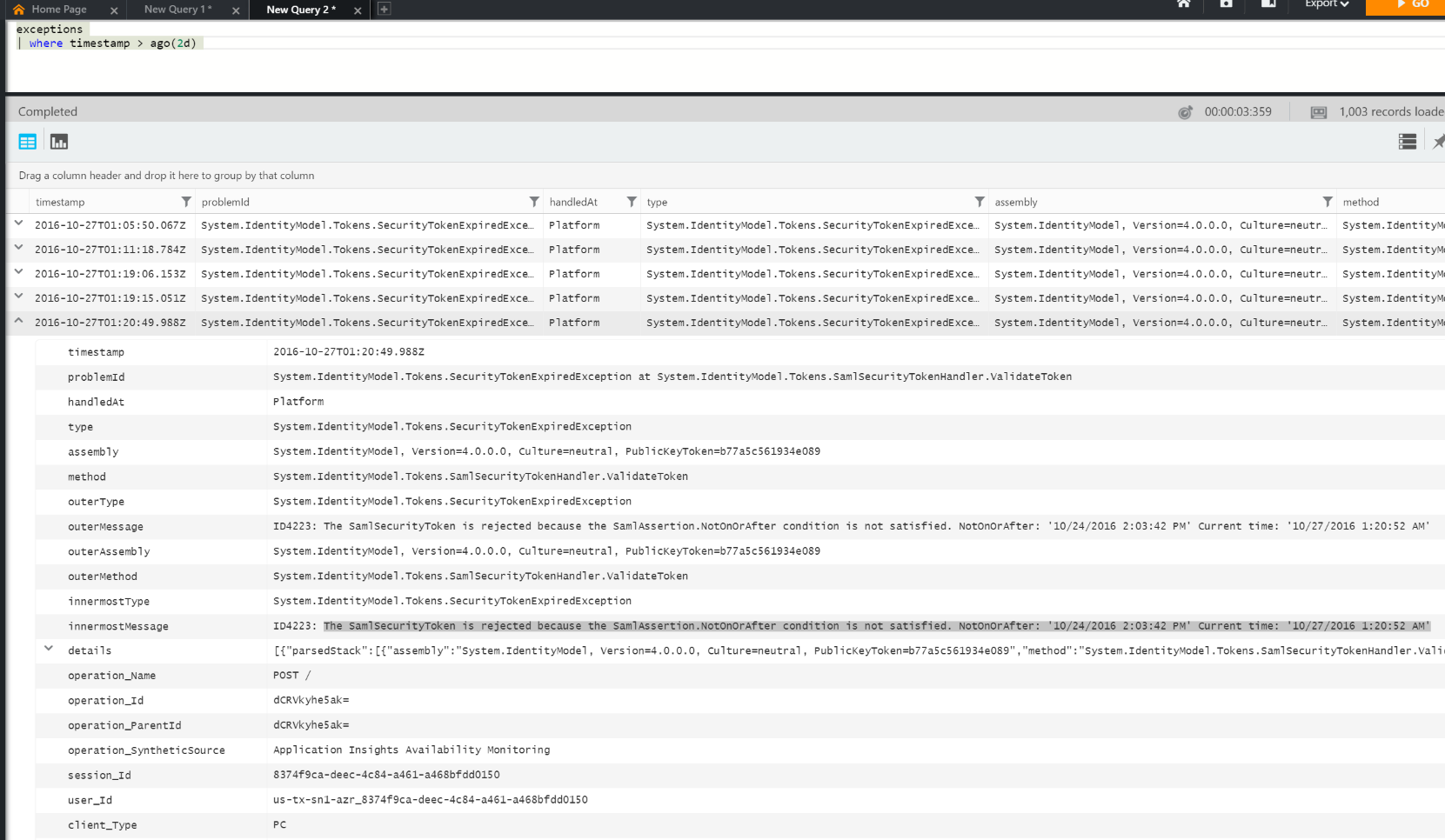
If you setup the multiple step web test with this script, after the token with a timestamp expired, you will see error message such as “System.IdentityModel.Tokens.SecurityTokenExpiredException at System.IdentityModel.Tokens.SamlSecurityTokenHandler.ValidateToken”, “The SamlSecurityToken is rejected because the SamlAssertion.NotOnOrAfter condition is not satisfied. NotOnOrAfter: ‘10/24/2016 2:03:42 PM’ Current time: ‘10/27/2016 1:20:52 AM’ “
Solution
Steps of ADFS login
Redirect to ADFS for login
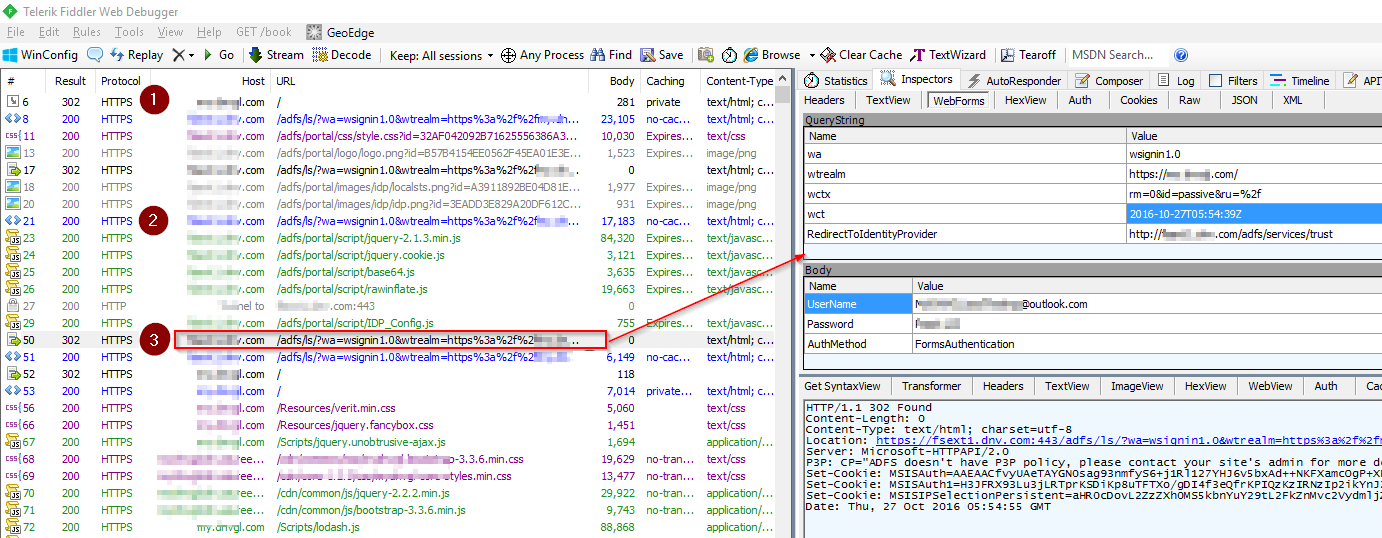
If the current session does not have an valid ADFS token, the end user will be automatically redirected to the ADFS login page. Pay attention to the hyperlink in the response body.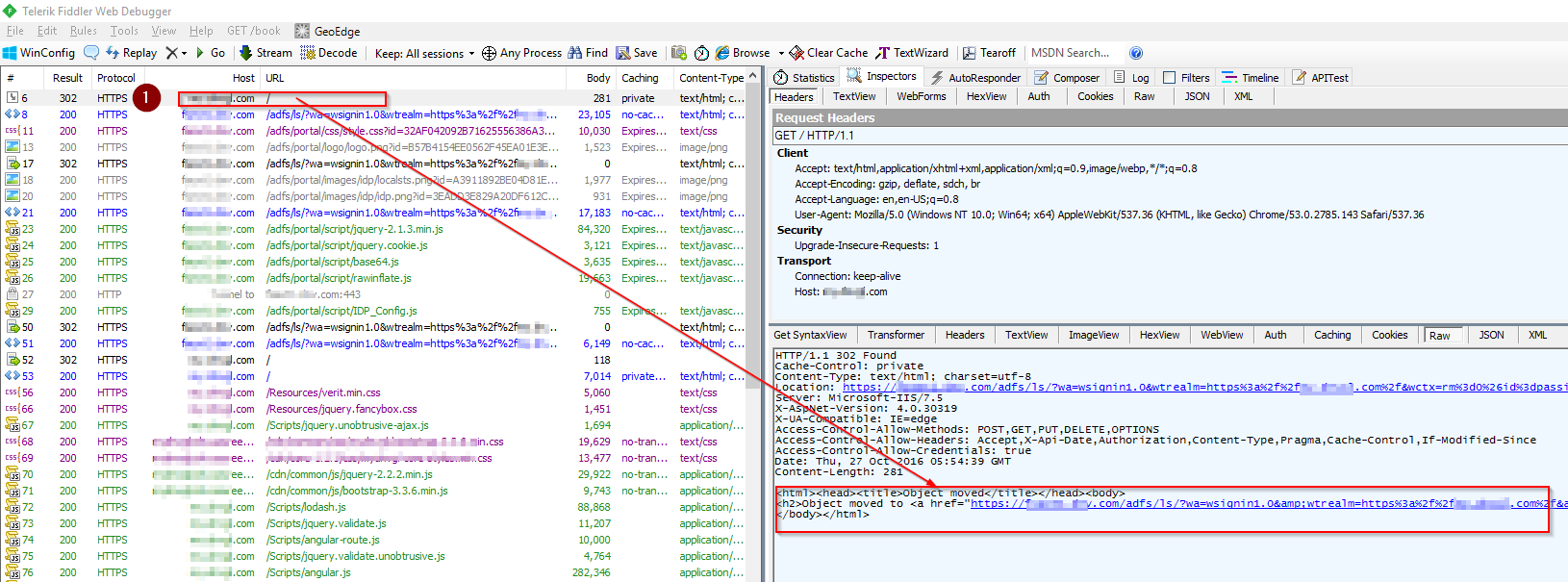
In the ADFS login form, user types the account name and password, then submit. The input values can be found in step 3 HTTP request body in below.
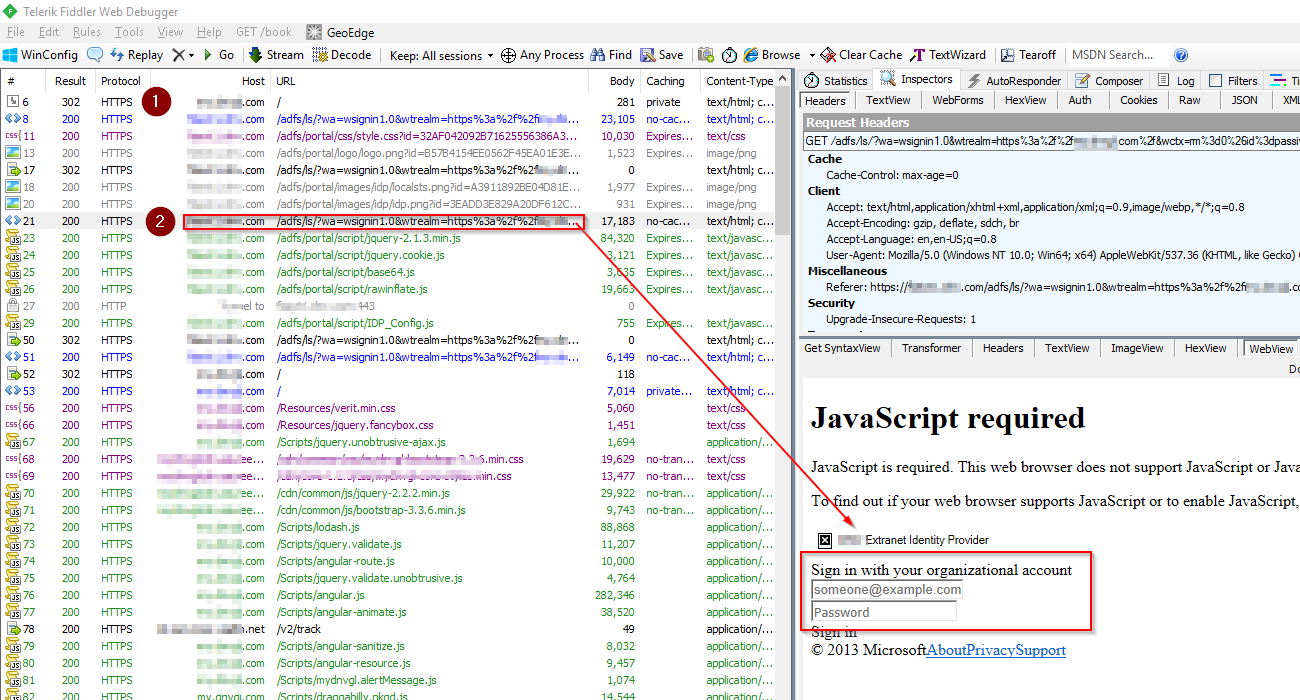
HTTP POST the user name and password to ADFS URL for verification.
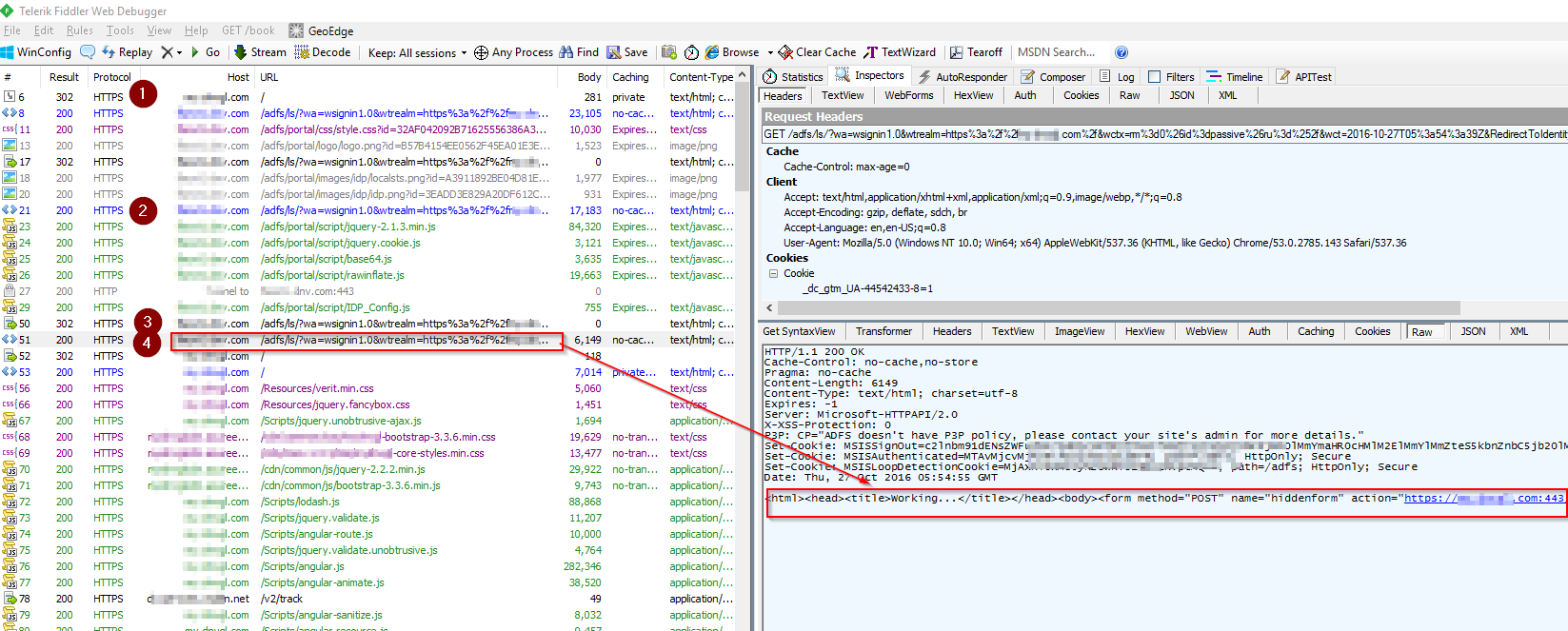
If the credential is valid, generate a response HTML which triggers a HTTP POST back to the application URL. The values in the HTTP POST can be found in Step 5 screenshot in below.
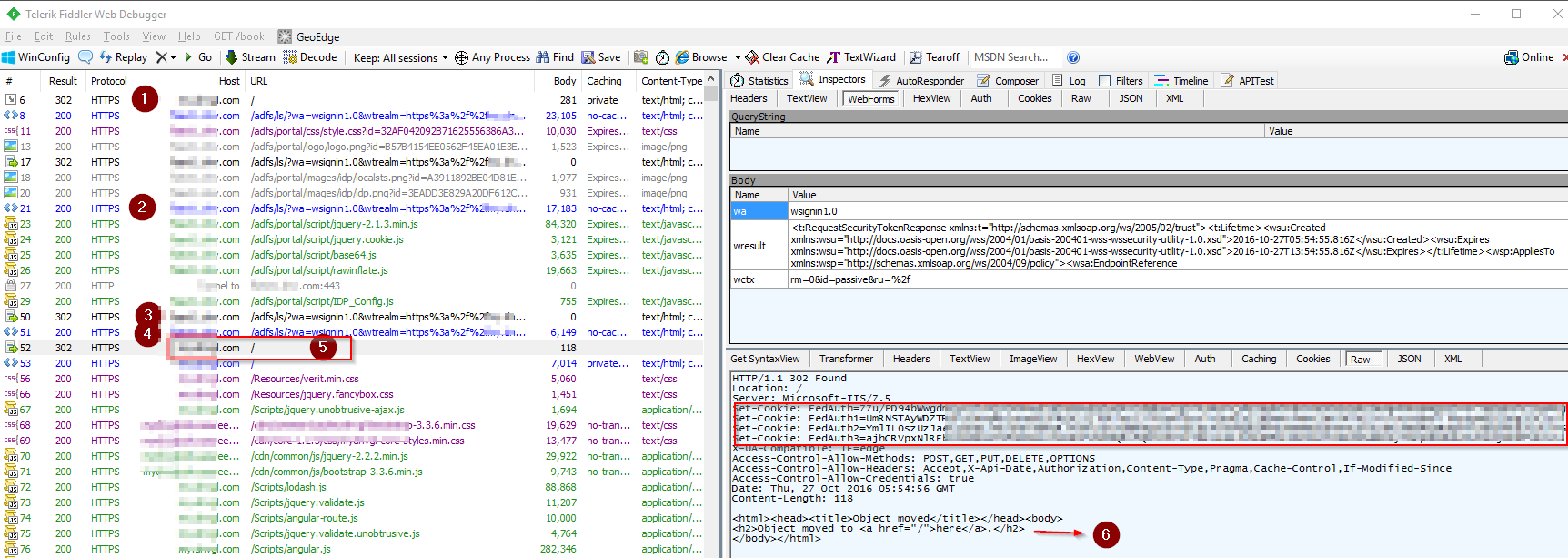
As the result of the generated HTTP POST to application URL, User got the authentication token to login
Setup script
In the script, we have following setup: (Please note that the script is accessing a specify application URL: “/notifications”, instead of the root URL “/“)
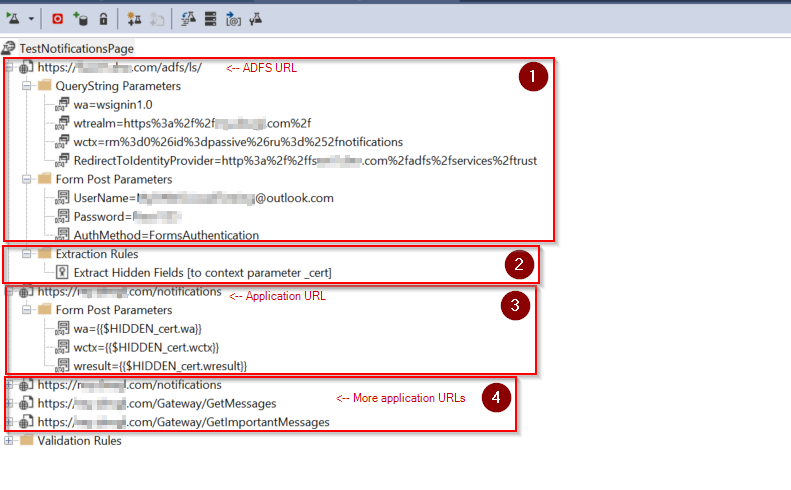
Conduct a directly POST call to ADFS URL
Querystring: values for protocol(wa), application information(wtrealm and wctx) and RedirectToIdentityProvider
Form: authenticaiton method, account name and passwordOnce we got the response, extract from context parameter _cert
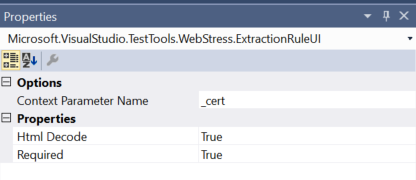
Conduct a directly POST call to application URL , with values that we extracted from previous call to ADFS
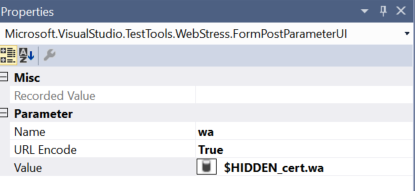
From now on, you can continue the testing with more URLs of the application, without passed values from hidden fields as we did in above.
Successed tests
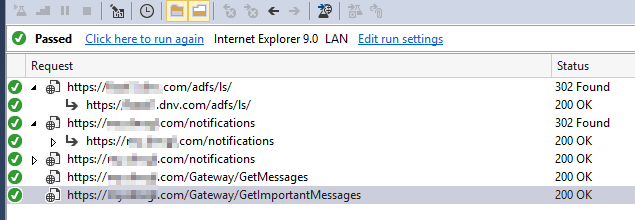
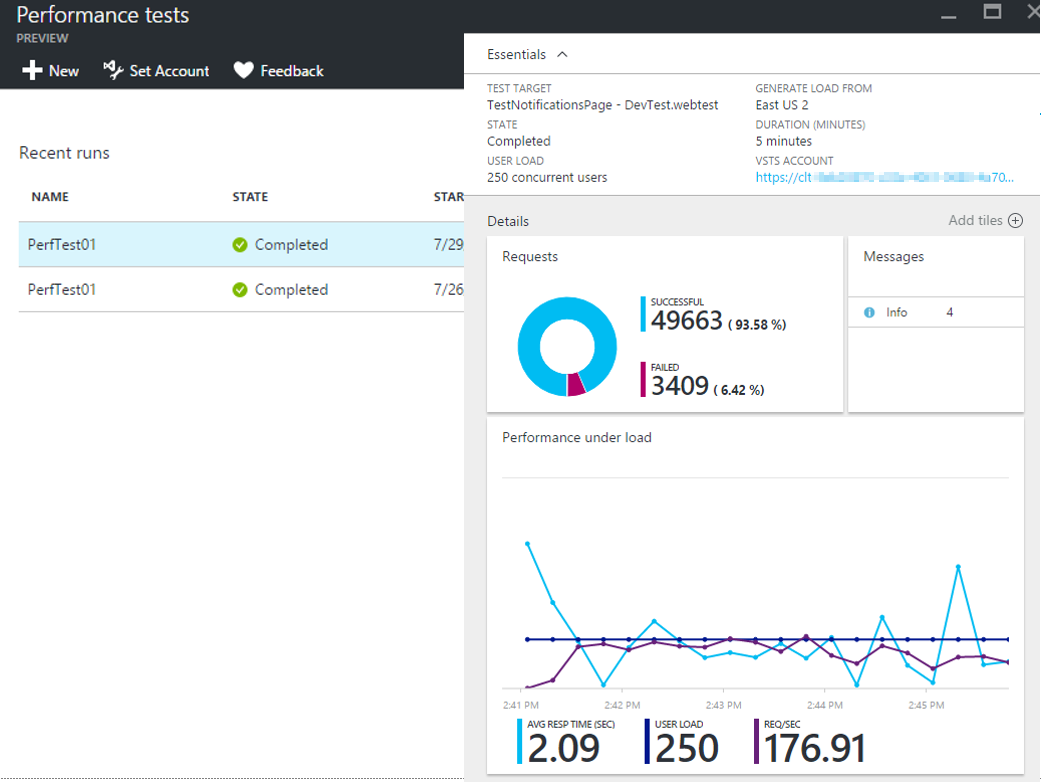
Load Testing
As far as the web testing script is ready, you can quickly load them into the load test cases.
Ref
There are two similar posts about authentication of ADFS: